The last five months we've been working on a shiny new version of our ASGARD platform that overcomes previous limitations and includes exciting new features. ASGARD 2 is a completely rewritten management platform, featuring a new interface, load balancing options, a...
Automated Citrix Netscaler Forensic Analysis with THOR
Update 14.02.2023 The information in this blog post is outdated. For more information on how to scan appliances remotely using SSH see this newer blog post. In this blog post I'd like to outline an idea on how to perform an automated compromise assessment on Citrix...
THOR Integration into Microsoft Defender ATP
Why Integrate THOR into Microsoft Defender ATP While Microsoft Defender ATP fully plays off its strength in detecting live attacks, suspicious process starts and network connections, THOR shines as a live forensic scanner that scans the local filesystem, registry,...
Not All IOC Scanning Is The Same
People often tell us that EDR product X already does IOC scanning and that they don’t have to check for these indicators a second time using our scanners. Especially when it comes to network wide sweeps for traces of activity due to an ongoing incident I recommend...
ASGARD Analysis Cockpit v2.8 with Sandbox Integration
ASGARD Analysis Cockpit’s new version 2.8.2 features an open API to interface with all major sandbox vendors. It ships with presets for Cuckoo Sandbox and even allows to connect multiple different sandboxes at the same time. Today users can configure THOR scans in...
Changes in Upcoming THOR Version 10.3
Refactored Handle Detection We have completely refactored THOR's malicious Handle detection. We now allow the use of regular expressions and combined all types in a single signature file named "malicious-handles.dat". Users can provide custom indicators by placing a...
THOR Remote Demo: Agentless Remote Compromise Assessment
We've made a short video demo to showcase the new THOR 10 feature called "THOR Remote", which allows you to perform compromise assessment scans on multiple remote systems - no agent or scripting required.
THOR 10 for AIX
We are working on a THOR scanner version that brings our well-known compromise assessments and thousands of YARA rules to IBM's AIX®. Subscribe here to get noticed once beta testing and a stable version is available. * no advertisements - just two emails, one for the...
THOR v10.2 Changes
New Module "Events" This module checks registered Events in the system environment as they are used by advanced malware and rootkits. We have checked for malicious Events before, in the Rootkit module, but these checks were hardcoded. We've spun out that section and...
Antivirus Event Analysis Cheat Sheet v1.7.2
We've just released an updated version of our Antivirus Event Analysis cheat sheet. You can download version 1.7.2 here. The major changes are: Updated AV signature lists Extended file extension list
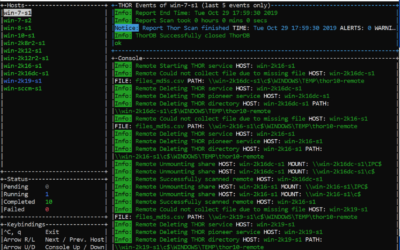
New Feature in THOR v10.1 – Remote Scanning
THOR v10.1 features a mode of operation that is especially helpful in incident response or compromise assessment scenarios - remote scanning. Imagine that you're in a firefighting scenario - a breach has been confirmed and management wants to have quick results on...
THOR 10 Fusion Released
THOR 10 Fusion has arrived. It replaces our successful scanners THOR 8 and SPARK and combines the best of both worlds. It is a completely new code base that features all modules of our 4 year old compromise assessment flagship THOR 8 and the speed and extra features...