This is the first blog post published on our new website. If you followed my blog on www.bsk-consulting.de you should consider subscribing to the RSS feed of this blog or the "Nextron Systems Newsletter". This is one of the YARA related blog posts showcasing a special...
YARA Rules to Detect Uncommon System File Sizes
YARA is an awesome tool especially for incident responders and forensic investigators. In my scanners I use YARA for anomaly detection on files. I already created some articles on "Detecting System File Anomalies with YARA" which focus on the expected contents of...
Synergetic Effects of Network and Host Based APT Detection
People often ask me if they still need our host based scanner THOR now that they have bought a network appliance that already checks all content that goes into and leaves their network. I normally answer that it is not a question of one solution versus another, but a...
APT Detection is About Metadata
People often ask me, why we changed the name of our scanner from "IOC" to "APT" scanner and if we did that only for marketing reasons. But don't worry, this blog post is just as little a sales pitch as it is an attempt to create a new product class. I'll show you why...
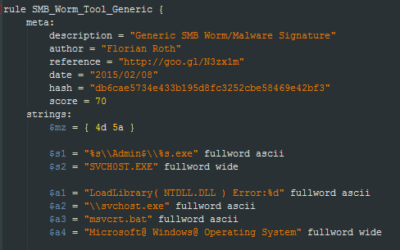
How to Write Simple but Sound Yara Rules
During the last 2 years I wrote approximately 2000 Yara rules based on samples found during our incident response investigations. A lot of security professionals noticed that Yara provides an easy and effective way to write custom rules based on strings or byte...
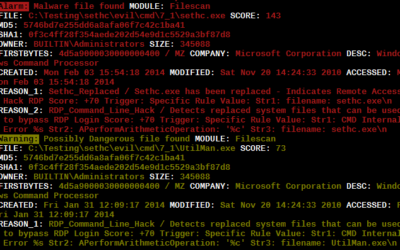
Inverse Yara Signature Matching (Part 1/2)
During our investigations we encountered situations in which attackers replaced valid system files with other system files to achieve persistence and establish a backdoor on the systems. The most frequently used method was the replacement of the "sethc.exe" with the...