may be configured centrally.
But what if a deployment of thousands of clients is planned? What if the Remote Access Client will be used in an ATM scenario and the deployment has to work without user interaction? Accepting the fingerprint automatically or let the user accept it is not a good choice from a security perspective.
A working solution for this challenge is to deploy the fingerprint together with the Remote Access Client. As the fingerprints are stored in the registry this is possible within a few steps.
But at first a little warning:
The registry key containing the gateway fingerprint is not deleted while the Remote Access Client is uninstalled. When testing auto installation software multiple times on the same system the fingerprint has to be deleted manually before running a test. Otherwise the fingerprint verification is skipped and the test results may be incorrect.
The registry key containing the fingerprints is:
HKEY_LOCAL_MACHINE\SOFTWARE\CheckPoint\accepted_cn\
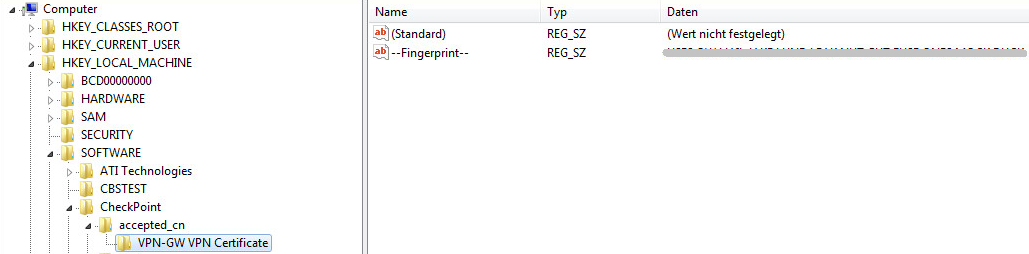
Registry Fingerprint
You may now export all fingerprints or a single fingerprint at your choice using the ordinary regedit context menu. The German word “Exportieren” at the figure means “export”.
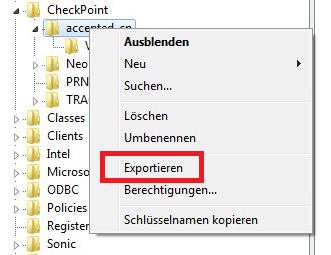
Registry Export
As a result you will get a .reg file that you may import on all systems that should know the fingerprint.
To sum all that up to a one click installation a simple two line batch script is sufficient to import the fingerprint and start the “E80.42 for ATM” installation.
regedit /S Fingerprint.reg CP_EPS_E80.42_RAC_Windows_ATM.msi /quit /forcerestart
This works for most auto deployments and avoids the necessity to verify the fingerprint on every new installation of the Remote Access Client.
Note: This has been tested using Check Point Remote Access Client E40.42 for ATM










