Endpoint-Driven Log Forwarding
One of the most important architectural aspects of this feature is where the forwarding occurs. It’s not the THOR Cloud platform that pushes logs to your SIEM—it’s the THOR scanner on each endpoint that performs this action. Once a scan completes, the local scanner connects to the configured destination and transmits the logs directly.
This offers significant advantages:
- Confidentiality: Logs remain inside your environment and do not pass through the cloud.
- Immediate availability: Data reaches your SIEM or analysis system as soon as the scan finishes.
- Reduced cloud dependencies: Ideal for regulated, segmented, or air-gapped environments.
However, there are trade-offs. Since forwarding occurs per endpoint, every host must be able to reach the destination (host, port, protocol). If delivery fails—due to firewall rules, DNS resolution issues, or TLS misconfiguration—the error will appear in the local scan log. There is no centralized retry mechanism: delivery success is per-endpoint and per-scan.
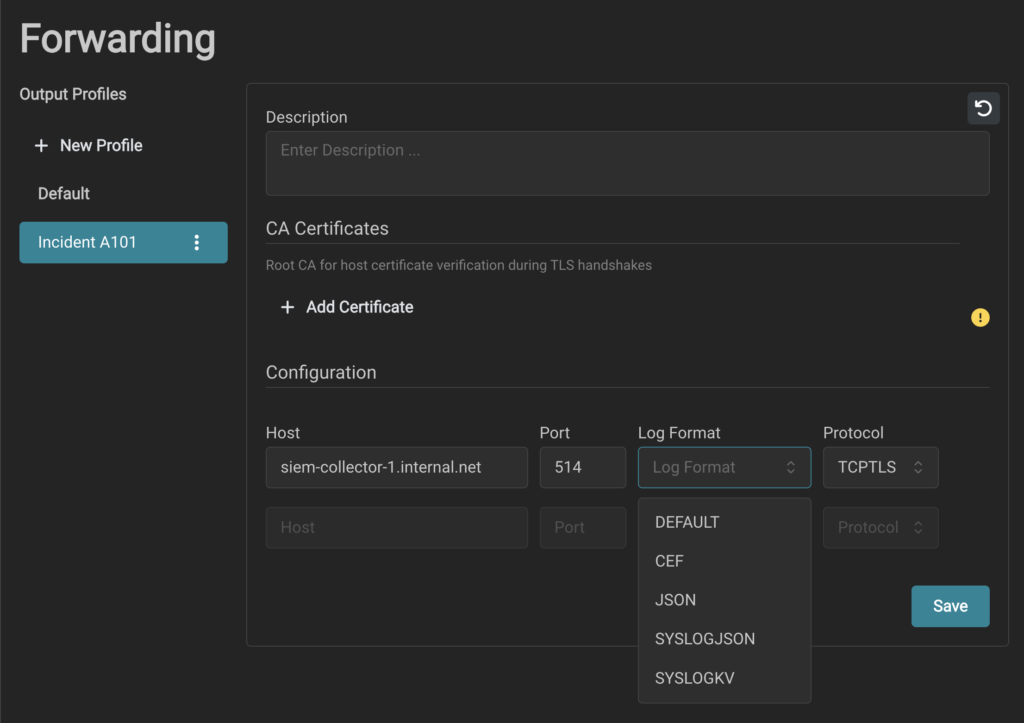
Profile Configuration and Use
Forwarding Profiles are configured in the THOR Cloud portal, under the dedicated “Forwarding” section. Each profile defines:
- One or more destination hosts (FQDN or IP)
- Port and protocol (TCP or UDP, with optional TLS)
- Log format: Syslog, JSON, or CEF
- (Optional) Root CA certificate for TLS-secured connections
You can maintain multiple profiles, each tailored to a specific use case—such as production vs. staging, or by region, business unit, or sensitivity level.
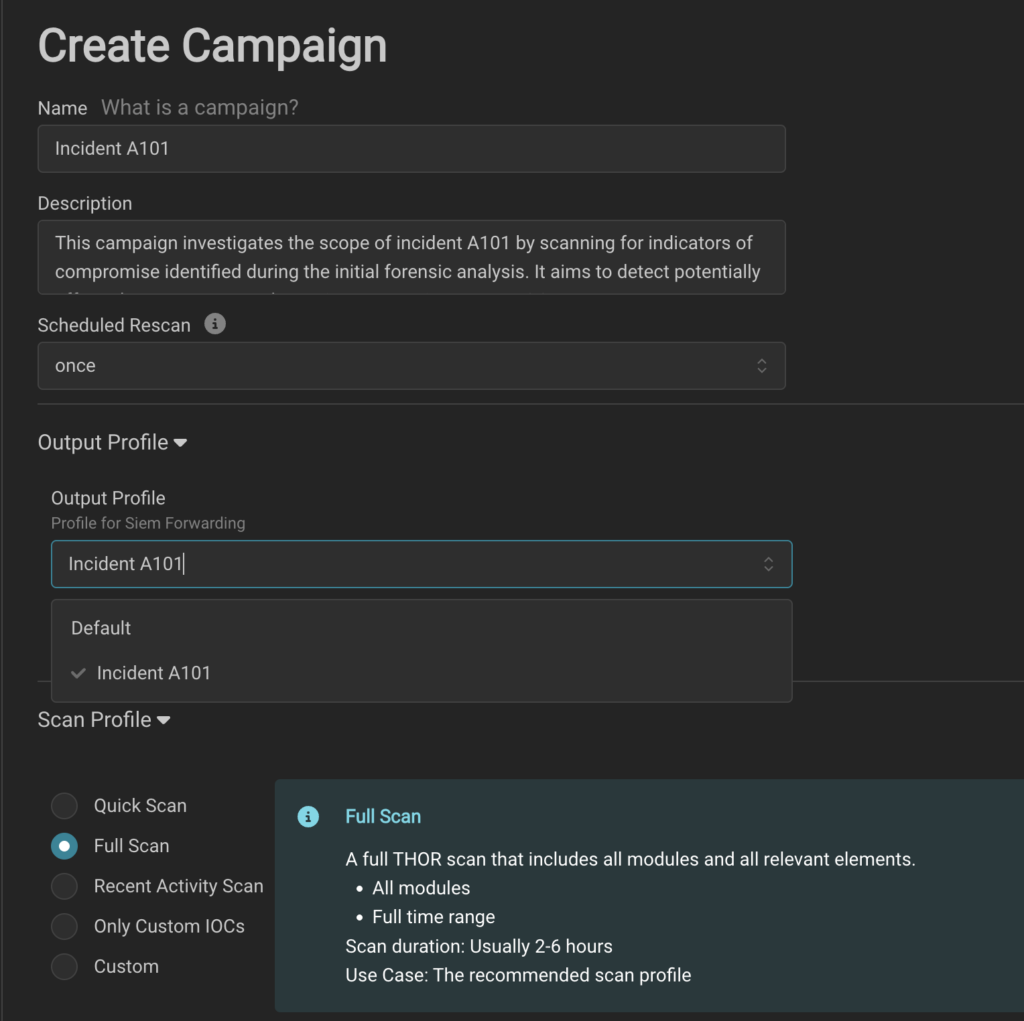
When launching a scan campaign, you’ll find a forwarding profile dropdown in the campaign configuration screen. If a default profile has been defined, it will be pre-selected automatically. This integration ensures that logs are consistently forwarded without requiring manual selection—though it’s easy to override if necessary.
Optional Log Storage Bypass
Every forwarding profile also supports an optional setting to disable cloud-based log storage. When enabled, THOR Cloud does not retain the results of a scan—the logs are forwarded only to the specified external systems. This is useful for scenarios in which data must not leave the local network or be retained in third-party environments.
Summary
Forwarding Profiles in THOR Cloud Enterprise offer a practical, secure, and flexible way to integrate forensic scan results into your centralized workflows. By pushing logs directly from the endpoint to your internal systems, you retain control over your data and reduce operational overhead. For distributed or compliance-focused environments, this change supports secure autonomy at scale—without compromising on visibility or traceability.
The feature is available now to all THOR Cloud Enterprise users. Please reach out to your Nextron contact if you require profile-based forwarding without THOR Cloud storage, or if you need guidance on setting up your internal receivers.










